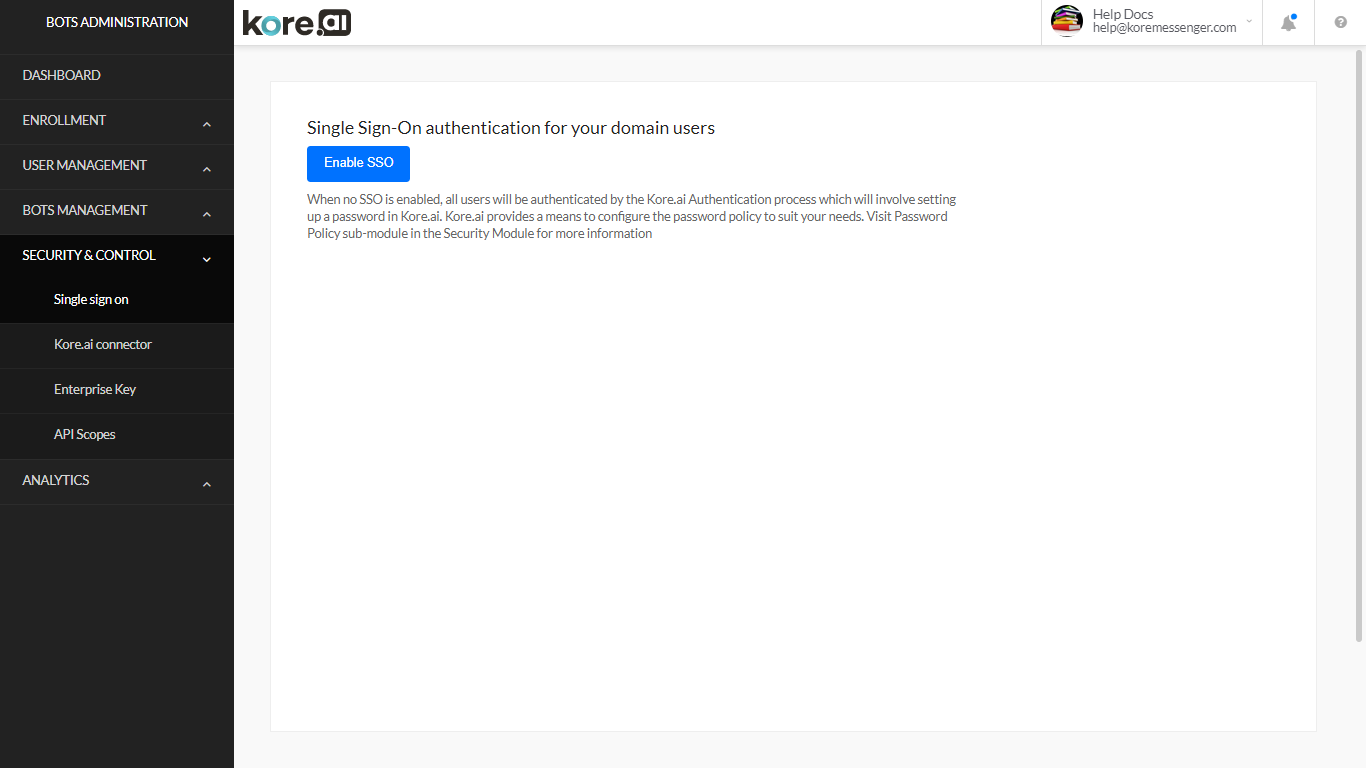
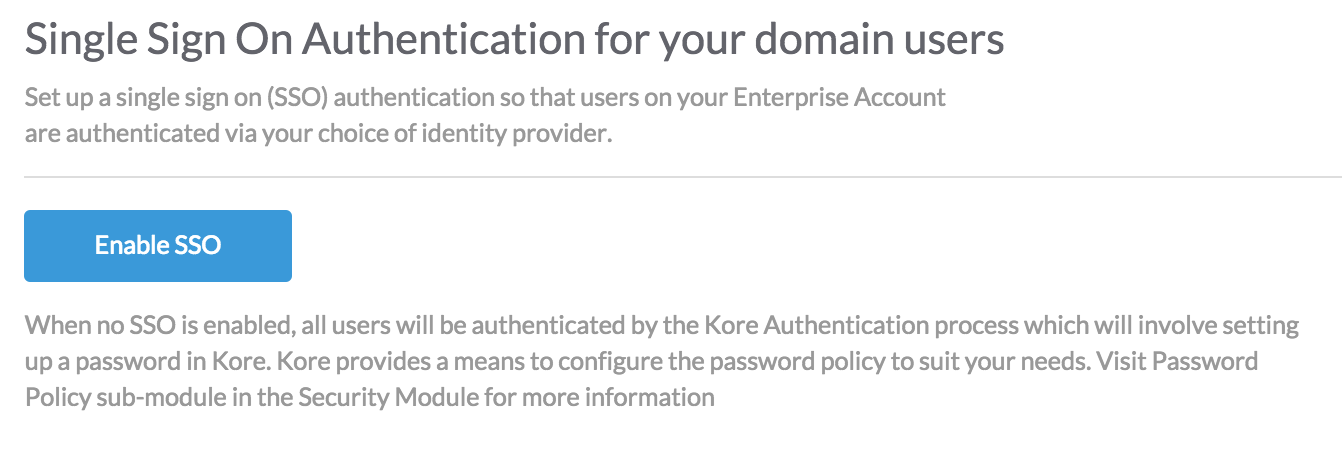
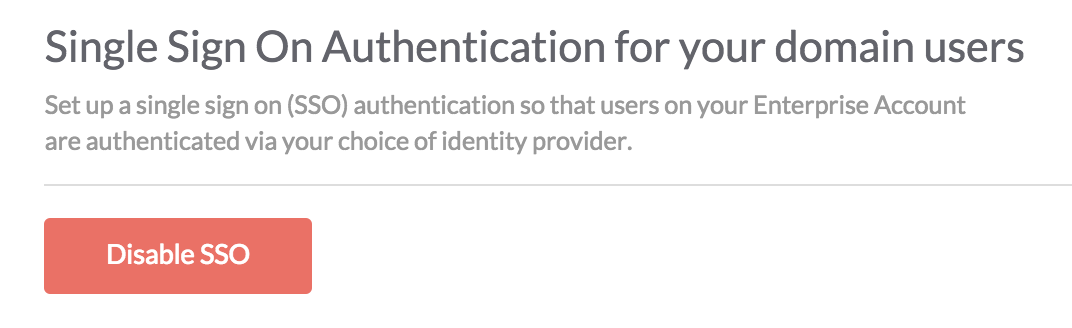
On the Kore.ai Single Sign-On page, in the Security & Control module of the Bots Admin Console, you can configure Single Sign-On (SSO)authentication for your Kore.ai managed users using the following:
- OpenID Connect
- Security Assertion Markup Language (SAML)
- WS-Federation sign-on protocol.
SSO enables easy access to the Kore.ai application using your existing identity provider. With SSO, your users can log on once, for example, to your company account, and when accessing their Kore.ai application, the same login credentials can be used automatically by the system.
For example, using the WS-Federation sign-on protocol, you can enable a user to sign on to the Kore.ai application using Microsoft® Active Directory® server credentials.
The following illustration shows the Single Sign-On page in the Bots Admin Console Security & Control module.
Enable or Disable SSO
Depending on the security required for your company, you can enable or disable Single Sign-On (SSO) for users accessing the Kore.ai application.
When you disable SSO or when the SSO authentication validity period expires, users must create and log on using their credentials. If no account specific password policies have been defined, then default Kore.ai password policies are automatically enabled for the users.
To enable Single Sign-On
To disable Single Sign-On
OpenID Connect
Complete the steps in the following procedure to configure SSO using Open ID Connect protocol in the Security & Control module of the Bots Admin Console. Kore.ai also supports WS-Federation and SAML Connect protocols.
- In the Security & Control module on the Single Sign On page in the Bots Admin Console, click Enable SSO.
- In the Select suitable Sign-On Protocol section, select OpenID Connect.
- In the Configure SSO for OpenID Connect section, select an identity provider, for example, Sign in with Google.
- Click Save.
- The Identity Provider information successfully updated message is displayed at the top of the page.
WS-Federation
Complete the steps in the following procedure to configure Single Sign-On (SSO) using the WS-Federation protocol in the Security & Control module of the Bots Admin Console.
- In the Security & Control module on the Single Sign On page in the Bots Admin Console, click Enable SSO.
- In the Select suitable Sign-On Protocol section, select WS-Federation.
- In the Configure SSO for WS-Federation section, select an identity provider, and then define the settings for:
- Windows Azure®
- Azure AD Sign-On End Point URL – The URL that Kore.ai sends sign on and sign off requests using Azure. The response for the authentication is sent to the Reply URL defined in your Azure Active Directory configuration settings.
- Azure AD Federation Metadata Document – The URL for the federation metadata document used for authentication with Azure Active Directory.
- Other – Generic WS-Federation identity provider configuration, other than Azure
- AD Sign-On End Point URL – The URL that Kore.ai sends sign on and sign off requests using your WS-Federation identity provider.
- AD Federation Metadata Document URL – The URL for the WS-Federation metadata document used for authentication with Active Directory.
- Windows Azure®
-
In the administrative console for your Single Sign-On provider, you will also need to define the URLs that are used to exchange data between Kore.ai and your SSO provider. While the URL names may vary by SSO provider, you will need to define these URLs:
- SAML 2.0
- LDAP Attribute: nameId
- Claim Attribute: uri
- SAML 1.1
- LDAP Attribute: nameId
- Claim Attribute: emailAddress
- Assertion Consumer Service (ACS) URL or Callback URL as https://idp.kore.com/authorize/callback.
- In addition to authentication values, you must pass the email address of the user as an LDAP attribute from Active Directory when using ADFS. For more information, see Attributes for ADFS.
- Click Save.
- SAML 2.0
The Identity Provider information successfully updated message is displayed at the top of the page.
SAML
Security Assertion Markup Language (SAML) is a standard protocol for web browser Single Sign-On (SSO) using secure tokens. SAML completely eliminates all passwords and instead uses standard cryptography and digital signatures to pass a secure sign-in token from an identity provider to a SaaS application.
SAML provides a solution to allow your identity provider and service providers to exist separately from each other. When a user logs into a SAML-enabled application, the service provider requests authorization from the appropriate identity provider. The identity provider authenticates the user’s credentials and then returns the authorization for the user to the service provider, and the user is now able to use the application.
How SAML works
SAML SSO works by transferring the user’s identity from one place (the identity provider) to another (the service provider). This is done through an exchange of digitally signed XML documents.
Consider the following scenario: A user is logged into a system that acts as an identity provider. The user wants to log in to a remote application, such as a support or accounting application (the service provider). The following happens:
- The user accesses the remote application using a link on an intranet, a bookmark, or similar and the application loads.
- The application identifies the user’s origin (by application subdomain, user IP address, or similar) and redirects the user back to the identity provider, asking for authentication. This is the authentication request.
- The user either has an existing active browser session with the identity provider or establishes one by logging into the identity provider.
- The identity provider builds the authentication response in the form of an XML-document containing the user’s username or email address, signs it using an X.509 certificate, and posts this information to the service provider.
- The service provider, which already knows the identity provider and has a certificate fingerprint, retrieves the authentication response and validates it using the certificate fingerprint.
- The identity of the user is established and the user is provided with app access.
Kore.ai Implementation
There are two ways SAML can be used within Kore.ai Bots Platform:
- For developer authentication to access the Bot Builder,
- For user authentication to access the Bot.
Use case 1: Bot builder authentication.
Enterprises can set up access to the Bot builder tool using the enterprise SSO. Bot developers and admins can log into bot builder using SSO done by the enterprise identity provider.
SSO flow from Kore.ai Bots platform: The following is the flow within the Kore.ai Bots platform once SSO is configured using SAML:
- The client makes a call to Kore app server (using the login URL) with user details to get identity provider info (SAML).
- Kore app server initiates a handshake request with the Kore idproxy server.
- Kore idproxy server initiates a request to the identity provider (SAML) with user details.
- On successful authentication, the identity provider (SAML) returns an assertion response to the Kore idproxy server.
- Upon verifying the response from the identity provider, Kore idproxy server initiates a request to the Kore app server.
- On successful authentication of the token from Kore idproxy server, Kore app server grants access to the user.
Post v7.2 release, Kore.ai supports the IDP initiated flow, wherein the platform gets the postback directly with SAML response and is able to validate the assertion and register/identify the user. The configuration for these modes – SP-based and IDP-based flow is different and is highlighted in the configuration steps below.
Refer below to configure SSO using SAML
Use case 2: End-user authentication
In this scenario, the bot chat interface is embedded on the customer portal or Mobile app that requires user authentication via SSO.
The Bot access is automatically limited to authenticated users. If the task requires API invocation that requires SSO based authentication the developer can follow the below steps
- On the client, developer needs to retrieve SSO token of the logged in user and pass it to the bot using the secureCustomPayload parameter in the Bot SDK API.
- In the dialog task, Bot developer can write custom logic to read this token and add it as API headers for secure API calls made using service node or webhook node.
The token information on the client varies depending upon the SSO provider and the payload, accordingly the developer would need to write custom logic.
Configuring SSO using SAML
Complete the following steps to configure Single Sign-On (SSO) using Security Assertion Markup Language (SAML) protocol in the Kore.ai Bots Admin Console. Kore.ai also supports WS-Federation and OpenID Connect protocols. For more information, see Using Single Sign-On.
OKTA Configuration
- In the Security & Control module on the Single Sign On page in the Bots Admin Console, click Enable SSO.
- In the Select a suitable Sign-On Protocol section, select SAML.
- In the Configure SSO for SAML section, select an identity provider, and then define the settings for one of:
- Okta Single Sign-On URL – The SSO URL for Okta this is to enable Service Provider initiated SAML flow.
- Identity Provider Issuer – The entity that provides the user identities including the ability to authenticate a user.
- Certificate – The public certificate stored by the service provider from the identity provider used to validate a user signature. You can add multiple (max of 2) certificates, delete already added invalid certificates, platform will use the latest certificate for authorization, in case it is invalid then the older certificate would be used.
- ACS URL for SP Initiated SAML Flow – This is the redirect URL for Service Provided initiated SAML flow.
- ACS URL for IDP Initiated SAML Flow – This is the account-specific URL for Identity Provided initiated SAML flow.
- SAML Attribute Mapping – Enable this option to map SAML Attributes with Kore.ai Group Names or Admin Roles Names. Once enabled, you can:
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Full Sync – Every time the user signs in, the platform will update the user’s Group and Role assignments based on the SAML Attributes present in the response. All existing assignments will be removed. Only the new group or role assignments as available in the SAML response will be assigned
- Inclusion Only – Every time the user signs in, the platform will only assign the new group or roles available in the SAML response. All existing assignments will be retained. New assignments will be added as available in the SAML responses
- define one or more mapping pairs. Each pair includes
- SAML Attribute Name – Name of the SAML attribute as available in the SAML response
- SAML Attribute Value – Value associated with the SAML attribute
- Attribute Type – Refers to the type of mapping to be associated i.e. Group Name or Role Name
- Group Name – Refers to any of the user groups defined in the Kore.ai account
- Role Name – Refers to the following
- Admin Roles defined in the Kore.ai account
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- Kore.ai Attribute – Refers to either Group Name or Role Name. The list should include the following:
- List of all Admin Roles
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Exclude RequestedAuthnContext in request – Enable this option to remove RequestedAuthnContext from SAML authentication requests.
Okta for Kore.ai SSO
To configure Single Sign-On in Okta for Kore.ai, you must first add the Kore.ai app to your Okta account, and then copy URLs and the security certificate from Okta into your Kore.ai account. This topic describes how to add the Kore.ai app to your Okta account, and then access the URLs and certificate needed for the Kore.ai configuration for SSO using Okta.
To complete this procedure, you must have already selected Okta as a SAML provider on the Single Sign On page in the Bots Admin Console.
To add the Kore.ai app to Okta- Log on to Okta.
- On the Home page, click Admin. The Dashboard page is displayed.
- On the top navigation bar, click Applications. The Applications page is displayed.
- Click Add Application. The Add Application page is displayed.
- Click Create application
- In the General settings, provide an App name and click Next.
- In Configure SAML, provide the Single SignOn URL. To obtain this:
- Login to Kore.ai Bot Builder Admin Console
- under Security & Control -> Single Sign on page
- after enabling SAML and selecting Okta
- ACS URL for SP Initiated SAML Flow field would contain the required URL.
- For on-prem accounts, the ACS URL for SP Initiated SAML Flow is displayed as https://idproxy-dev.kore.com/authorize/callback . This needs to be updated as “single sign on URL” in Okta platform and https://idproxy-dev.kore.com needs to be updated as the “Audience URL”
- You can provide the Attribute statements like emailId, firstName as per your requirement.
- To configure ACS URL for IDP Initiated SAML Flow, copy and paste the complete URL that get from your admin. In case you are using internal redirection URLs, please reach out to your internal admin/network teams.
To get the ACS URL for IDP Initiated SAML Flow URL, check “User this Recipient URL and Destination URL”.
Enter the Audience URI field as ACS URL for SP Initiated SAML Flow (https://idp.kore.com/authorize/callback).
Note: This URL is a temporary URL. Once you add the Kore.ai app in Okta, this URL changes as per your organizations domain requirements. You must copy the final ACS URL again and paste in the field. For more information, read How to configure Okta SSO in Kore.ai XO Platform community post. - Click Finish.
- On the Sign On tab, in the Settings section, click View Setup Instructions. The How to Configure SAML 2.0 for <app-name> Application page is displayed.
- Copy the URLs in the:
- Identity Provider Single Sign-On URL field to the Okta Single Sign-On URL field in Kore.ai.
- Identity Provider Issuer field to the Kore.ai Identity provider issuer field
- In the Okta X.509 Certificate field, copy the certificate data, and then paste the data into the Kore.ai Certificate text box.
Note: Only data after the —–BEGIN CERTIFICATE—– header and before the —–END CERTIFICATE—- footer should be copied and pasted into Kore.ai.
- In Kore.ai, click Save. This will complete the integration of Okta login.
The Identity Provider information successfully updated message is displayed at the top of the page. To test the configuration, log off the Kore.ai Bots Admin Console, and log on again. The Okta portal should be displayed.
OneLogin Configuration
- OneLogin – For more information, refer below, or in the OneLogin documentation, see Configuring SSO for Kore.ai.
-
- SAML 2.0 Endpoint – The HTTP SSO endpoint for OneLogin to enable Service Provider initiated SAML flow, for example, https://app.onelogin.com/trust/saml2/http-post/sso/358111.
- Issuer URL – The URL for the OneLogin issuer, for example,https://app.onelogin.com/saml/metadata/358111.
- X.509 Certificate – The public certificate stored by the service provider from the identity provider used to validate a user signature. You can add multiple (max of 2) certificates, delete already added invalid certificates, platform will use the latest certificate for authorization, in case it is invalid then the older certificate would be used.
- ACS URL for SP Initiated SAML Flow – This is the redirect URL for Service Provided initiated SAML flow.
- ACS URL for IDP Initiated SAML Flow – This is the account-specific URL for Identity Provided initiated SAML flow.
- SAML Attribute Mapping – Enable this option to map SAML Attributes with Kore.ai Group Names or Admin Roles Names. Once enabled, you can:
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Full Sync – Every time the user signs in, the platform will update the user’s Group and Role assignments based on the SAML Attributes present in the response. All existing assignments will be removed. Only the new group or role assignments as available in the SAML response will be assigned
- Inclusion Only – Every time the user signs in, the platform will only assign the new group or roles available in the SAML response. All existing assignments will be retained. New assignments will be added as available in the SAML responses
- define one or more mapping pairs. Each pair includes
- SAML Attribute Name – Name of the SAML attribute as available in the SAML response
- SAML Attribute Value – Value associated with the SAML attribute
- Attribute Type – Refers to the type of mapping to be associated i.e. Group Name or Role Name
- Group Name – Refers to any of the user groups defined in the Kore.ai account
- Role Name – Refers to the following
- Admin Roles defined in the Kore.ai account
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- Kore.ai Attribute – Refers to either Group Name or Role Name. The list should include the following:
- List of all Admin Roles
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Exclude RequestedAuthnContext in request – Enable this option to remove RequestedAuthnContext from SAML authentication requests.
OneLogin for Kore.ai SSO
To configure Single Sign-On in Kore.ai using OneLogin, you must first add the Kore.ai app to your OneLogin account, and then copy URLs and the security certificate from OneLogin into your Kore.ai account. This topic describes how to add the Kore.ai app to your OneLogin account, and then access the URLs and certificate needed for the Kore.ai configuration for SSO using OneLogin.
To complete this procedure, you must have already selected OneLogin as a SAML provider on the Single Sign On page in the Bots Admin Console.
To add the Kore.ai app to OneLogin- Log on to OneLogin.
- On the APPS menu, click Add Apps. The Find Applications page is displayed.
- In the Search field, enter Kore.ai, and then press Enter. The Kore.ai app for OneLogin is displayed.
- Click the Kore.ai app. The Add Kore.ai page is displayed.
- Optionally, change the display name or the icons displayed to your users in the OneLogin portal, and then click SAVE. The Kore.ai app is added to your Company apps for OneLogin and the Kore.ai app page is displayed.
- On the SSO tab, in the Enable SAML2.0 section, copy the URLs in the:
- OneLogin SAML 2.0 Endpoint (HTTP) field to the Kore.ai SAML 2.0 Endpoint field
- OneLogin Issuer URL field to the Kore.ai Issuer URL field
- In the OneLogin X.509 Certificate field, click View Details. The Standard Strength Certificate (2048-bit) page is displayed.
- In the X.509 Certificate section, copy the certificate data, and then paste the data into the Kore.ai X.509 Certificate text box.
Note: Only data after the —–BEGIN CERTIFICATE—–header and before the —–END CERTIFICATE—- footer should be copied and pasted into Kore.ai.
- In Kore.ai, click Save.
The Identity Provider information successfully updated message is displayed at the top of the page. To test the configuration, log off the Kore.ai Bots Admin Console, and log on again. The OneLogin portal should be displayed.

Bitium Configuration
-
- Single Sign-On URL – The HTTP SSO endpoint for Bitium to enable Service Provider intiated SAML flow, for example, https://www.bitium.com/7655.
- Issuer URL – The URL for the OneLogin issuer, for example,https://bitium.com/7655/saml/82456/metadata.xml.
- Certificate – The public certificate stored by the service provider from the identity provider used to validate a user signature. You can add multiple (max of 2) certificates, delete already added invalid certificates, platform will use the latest certificate for authorization, in case it is invalid then the older certificate would be used.
- ACS URL for SP Initiated SAML Flow – This is the redirect URL for Service Provided initiated SAML flow.
- ACS URL for IDP Initiated SAML Flow – This is the account-specific URL for Identity Provided initiated SAML flow.
- SAML Attribute Mapping – Enable this option to map SAML Attributes with Kore.ai Group Names or Admin Roles Names. Once enabled, you can:
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Full Sync – Every time the user signs in, the platform will update the user’s Group and Role assignments based on the SAML Attributes present in the response. All existing assignments will be removed. Only the new group or role assignments as available in the SAML response will be assigned
- Inclusion Only – Every time the user signs in, the platform will only assign the new group or roles available in the SAML response. All existing assignments will be retained. New assignments will be added as available in the SAML responses
- define one or more mapping pairs. Each pair includes
- SAML Attribute Name – Name of the SAML attribute as available in the SAML response
- SAML Attribute Value – Value associated with the SAML attribute
- Attribute Type – Refers to the type of mapping to be associated i.e. Group Name or Role Name
- Group Name – Refers to any of the user groups defined in the Kore.ai account
- Role Name – Refers to the following
- Admin Roles defined in the Kore.ai account
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- Kore.ai Attribute – Refers to either Group Name or Role Name. The list should include the following:
- List of all Admin Roles
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Exclude RequestedAuthnContext in request – Enable this option to remove RequestedAuthnContext from SAML authentication requests.
Kore.ai SSO for Bitium
To configure Single Sign-On in Bitium for Kore.ai, you must first add the Kore.ai app to your Bitium account, and then copy URLs and the security certificate from Bitium into your Kore.ai account. This topic describes how to add the Kore.ai app to your Bitium account, and then access the URLs and certificate needed for the Kore.ai configuration for SSO using Bitium.
To complete this procedure, you must have already selected Bitium as a SAML provider on the Single Sign On page in the Bots Admin Console.
To add the Kore.ai app to Bitium- Log on to Bitium.
- On the Manage < Company Name > menu, click Manage Apps, then click Add an App. The Add Apps dialog is displayed.
- In the Search field, enter Kore.ai, and then press Enter. The Install Kore.ai app for Bitium dialog is displayed.
- On the Manage Organization menu, click Manage Apps, and then click Kore.ai.
- On the Single Sign-On tab, in the Select a Single Sign-On Provider section, select SAML Authentication.
- Copy the following URLs from Bitium into the Bots Admin Console Bitium configuration section:
- Bitium Login URL field to the Kore.ai Single Sign-On field
- Bitium Logout URL field to the Kore.ai Issuer URL field
- In the Bitium X.509 Certificate field, copy the certificate data, and then paste the data into the Bots Admin Console Certificate text box.
Note: Only data after the —–BEGIN CERTIFICATE—– header and before the —–END CERTIFICATE—- footer should be copied and pasted into Kore.ai.
- In Kore.ai, click Save.
The Identity Provider information successfully updated message is displayed at the top of the page. To test the configuration, log off the Kore.ai Bots Admin Console, and log on again. The Bitium portal should be displayed.
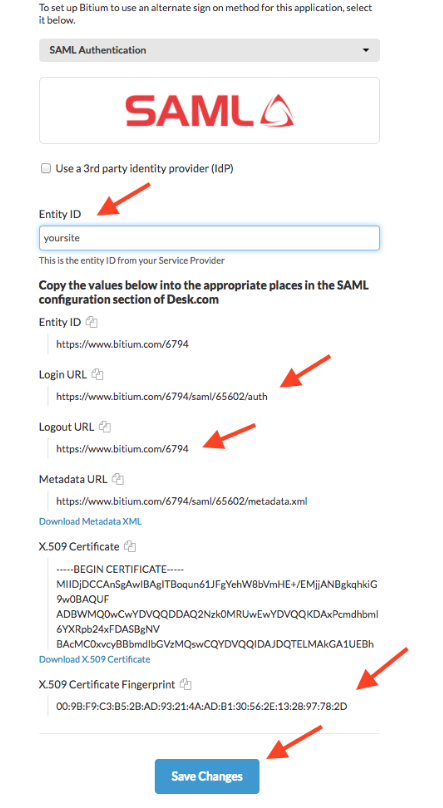
- Other – Generic SAML identity provider configuration. Select this option if you are not using a Kore.ai built-in configuration.
- Single Sign-On URL – The URL that Kore.ai sends sign on and sign off requests using your WS-Federation identity provider. This is to enable Service Provider initiated SAML flow.
- Issuer URL – The URL for the WS-Federation metadata document used for authentication with Active Directory.
- Certificate – The public certificate stored by the service provider from the identity provider used to validate a user signature. You can add multiple (max of 2) certificates, delete already added invalid certificates, platform will use the latest certificate for authorization, in case it is invalid then the older certificate would be used.
- ACS URL for SP Initiated SAML Flow – This is the redirect URL for Service Provided initiated SAML flow.
- ACS URL for IDP Initiated SAML Flow – This is the account-specific URL for Identity Provided initiated SAML flow.
- SAML Attribute Mapping – Enable this option to map SAML Attributes with Kore.ai Group Names or Admin Roles Names. Once enabled, you can:
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Full Sync – Every time the user signs in, the platform will update the user’s Group and Role assignments based on the SAML Attributes present in the response. All existing assignments will be removed. Only the new group or role assignments as available in the SAML response will be assigned
- Inclusion Only – Every time the user signs in, the platform will only assign the new group or roles available in the SAML response. All existing assignments will be retained. New assignments will be added as available in the SAML responses
- define one or more mapping pairs. Each pair includes
- SAML Attribute Name – Name of the SAML attribute as available in the SAML response
- SAML Attribute Value – Value associated with the SAML attribute
- Attribute Type – Refers to the type of mapping to be associated i.e. Group Name or Role Name
- Group Name – Refers to any of the user groups defined in the Kore.ai account
- Role Name – Refers to the following
- Admin Roles defined in the Kore.ai account
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- Kore.ai Attribute – Refers to either Group Name or Role Name. The list should include the following:
- List of all Admin Roles
- Bot Builder Access
- New Bot Creation
- Manage Data Tables and Views
- In the administrative console for your Single Sign-On provider, you will also need to define the URLs that are used to exchange data between Kore.ai and your SSO provider. While the URL names may vary by SSO provider, you will need to define these URLs:
- Assertion Consumer Service (ACS) URL or Callback URL as https://idp.kore.com/authorize/callback.
- In addition to authentication values, you must pass the email address of the user as an LDAP attribute from Active Directory when using ADFS. For more information, see Attributes for ADFS.
- Identity URL or Sign On URL as https://idp.kore.com
- define how the SAML attributes should be mapped with Kore.ai attributes:
- Click Save.
The Identity Provider information successfully updated message is displayed at the top of the page.
-
Attributes for ADFS
When you configure Single Sign-On using LDAP for ADFS, in addition to authentication attributes, your third-party SSO provider can send additional attributes to Kore.ai through the Assertion Consumer Service (ACS) URL or Callback URL.
If you are using a built-in Kore.ai app for SSO, such as Windows Azure for WS-Federation protocol, or OneLogin for SAML protocol, required attributes are already configured for Kore.ai when you add the Kore.ai app to your SSO provider admin console.
The following data is an example of attribute data passed to Kore.ai in the callback URL.
<Attribute Name="FirstName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="First Name"> <AttributeValue>Michael</AttributeValue> </Attribute> <Attribute Name="LastName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Last Name"> <AttributeValue>Mehra</AttributeValue> </Attribute> <Attribute Name="DisplayName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Display Name"> <AttributeValue>Michael Mehra</AttributeValue> </Attribute> <Attribute Name="EmailAddress" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Email"> <AttributeValue>michael.mehra@acme.com</AttributeValue> </Attribute>
These attributes are optional except for the EmailAddress, which is required. The Email Address attribute uses the following nameId format:
SAML 2.0: NameID Format="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" SAML 1.1: NameID Format="urn:oasis:names:tc:SAML:1.1:nameid:format:emailAddress
Mapping Attributes in ADFS
ADFS is a service provided by Microsoft as a standard role for Windows Server that provides a web login using existing Active Directory credentials. When using SAML or WS-Federation protocols to log on with ADFS, you can pass other values in addition to the authentication values.
The attribute values are defined as Claim Rules in the Relying Party Trust dialog in the SQL Server admin console. To edit the Claim Rules, select the Relying Party Trusts folder in ADFS Management, and then click Edit Claim Rules from the Actions sidebar. To add a new rule, click Add Rule, and then select the Send LDAP Attributes template. Enter the following mapping values:
- SAML 2.0
- LDAP Attribute: nameId
- Claim Attribute: uri
- SAML 1.1
- LDAP Attribute: nameId
- Claim Attribute: emailAddress
Logging On Using Your Admin Password Instead of SSO
As an Bots Admin, you can enable Single Sign-On (SSO) using a third-party security system, for example, Google. If for some reason, your SSO security system fails, or you forget your SSO log on credentials for your third-party security system, you can still log on to the Kore.ai Bots Admin Console and bypass SSO.
A Bots Admin with a custom admin role can only bypass SSO and use their admin password if custom privileges are enabled for at least one module. To log on to the Kore.ai Directory Agent, the custom admin must have privileges enabled for Enrollment – Directory Sync.
Before you can enable SSO, the Bots Admin must have logged on the Bots Admin Console using the log on credentials provided when signing up. After the Bots Admin configures and enables SSO, you can still access the Bots Admin Console directly at the following URL:
The following log on page is displayed and using your Bots Admin password credentials, you can log on to the Bots Admin Console and bypass SSO, if enabled.

If you cannot remember your Bots Admin password, enter your email ID, and then click the Forgot your password? link shown in the previous image. An email is sent to your Kore.ai email account with instructions on how to reset your Bots Admin password.
Logging Off
When you are finished with your session with the Bots Admin Console, you should log off the console and close your session to keep your bots account secure. To log off, click on your user name, and then click Logout as shown in the following illustration.
If your Bots Admin Console session is idle for more than 15 minutes, your session is automatically terminated, and the next action in the session window will open the Kore.ai web client instead. To start a new session, click the Bots Admin Console ![]() icon and log on.
icon and log on.