Bring Your Own Key (BYOK) encryption in Kore’s public cloud SaaS enables enterprises to retain complete control over their encryption keys while protecting sensitive data. With BYOK, organizations use their own Customer Master Keys (CMKs) to encrypt application and bot data, ensuring stronger security and compliance.
Kore’s BYOK solution integrates with external key management systems such as AWS Key Management Service (KMS). Customers retain ownership of their encryption keys while leveraging Kore’s secure, scalable cloud platform with HSM-backed keys.
Prerequisites
- Active Kore.ai subscription (platform.kore.ai) with BYOK enabled.
- AWS account with administrative access to IAM and KMS.
- Permissions to create IAM roles and policies.
- Permissions to create and manage KMS keys.
Information Exchange
The BYOK integration requires coordination between you (the customer) and the Kore.ai support team. Key information exchanged between Kore.ai and you is summarized in the table.
| Information | Description and Purpose | Provided By |
| Service Role ARN | The Amazon Resource Name (ARN) of the IAM role in Kore.ai’s AWS account. You add this to your IAM role’s trust policy to allow Kore.ai’s service to assume your role.
Service Role ARN for platform.kore.ai: arn:aws:iam::358587034707:role/SegBots-Servers-Role Note: Contact Kore.ai Support if your SaaS instance differs from platform.kore.ai. |
Kore.ai |
| External ID | A unique identifier (similar to a password) that Kore.ai uses when assuming your IAM role to prevent unauthorized access. External ID is auto-populated within the Bot Admin Console. |
Kore.ai |
| Role ARN | The ARN of the IAM role created in your AWS account. Kore.ai assumes this role to access your KMS key.
Example: arn:aws:iam::<your-account-id>:role/BYOK_Role Share this with Kore.ai after completing the steps in the Integration Process section. |
Customer |
| CMK ARN | The ARN of your Customer Managed Key (CMK) in AWS KMS. This key is used by Kore.ai to encrypt and decrypt your data.
Example: arn:aws:kms:<region>:<your-account-id>:key/<key-id> Follow the steps in the Integration Process section to create and share this value. |
Integration Process
The BYOK integration involves six main steps:
- Create IAM Policy: Define KMS permissions (encrypt, decrypt, generate keys, describe key).
- Create IAM Role: Establish a trust relationship with Kore.ai and attach the IAM policy.
- Create KMS Key: Set up a Customer Managed Key for encryption operations.
- Update KMS Key Policy: Grant the IAM role explicit access to use the KMS key.
- Verify Configuration: Confirm all components are correctly configured.
- Share Information: Provide your Role ARN and CMK ARN to Kore.ai support.
Step 1: Create IAM Policy
This policy defines the KMS permissions for your BYOK role.
1. Go to AWS Console → IAM → Policies.
2. Click Create policy.
3. Select the JSON tab and paste this policy:
{ "Version": "2012-10-17",
"Statement": [
{
"Sid": "BYOK KMSPermissions",
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "arn:aws:kms:REGION:ACCOUNT_ID:key/KEY_ID"
}
]
}
4. Click Next.
5. Name the policy (e.g., BYOK_KMS_Policy).
6. Add an appropriate description, for example: “Policy granting KMS permissions for BYOK integration with Bot Admin Console”.
7. Click Create policy.
| Note: Replace REGION, ACCOUNT_ID, and KEY_ID with your values. You can use “Resource”: “*” initially and update it after creating your KMS key. |
Step 2: Create IAM Role
This role establishes trust with Kore.ai and uses the policy from Step 1.
- Go to AWS Console → IAM → Roles.
- Click Create role.
- Select AWS Account as the trusted entity type.
- Select This account.
- Click Next.
- Select the BYOK_KMS_Policy from Step 1.
- Click Next.
- Name the role (e.g., BYOK_Role).
- Add an appropriate description, for example: “Role for BYOK integration with Bot Admin Console.”
- Click Create role.
Update Trust Policy
Configure the role to trust Kore.ai’s Service Role:
- Go to the BYOK_Role you just created.
- Click the Trust relationships tab.
- Click Edit trust policy.
- Replace the policy with the following:
- Click Update policy.
Step 3: Create KMS Key
Create a Customer Managed Key for encryption.
- Go to AWS Console → KMS → Customer managed keys.
- Click Create key.
- Select Symmetric as the key type.
- Select Encrypt and decrypt as the key usage.
- Click Next.
- Enter key details:
- An Alias (e.g.,
byok-kore-ai-key). - An appropriate Description, for example: “Customer managed key for BYOK integration with Bot Admin Console.
- An Alias (e.g.,
- Click Next.
- Under Key administrators, add your administrator users or roles as those who should manage this key.
- Click Next.
- Add the BYOK_Role as a key user.
- Click Next.
- Review the key configuration and click Finish.
Step 4: Update KMS Key Policy
Add the BYOK_Role to the key policy to grant explicit access.
- Go to your KMS key.
- Click the Key policy tab.
- Click Edit.
- Add the customer role statement to the existing Statement array (don’t remove other statements).
{ "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::ACCOUNT_ID:role/BYOK_Role" }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }Note
Replace ACCOUNT_ID with your AWS account ID.
- Save the policy.
Step 5: Verify Configuration
Confirm all components are correctly configured:
| Item | Verification |
| IAM Policy | Confirm BYOK_KMS_Policy exists with correct KMS actions. |
| Policy Attachment | Verify policy is attached to BYOK_Role under the Permissions tab. |
| Trust Relationship | Confirm the Trust relationships tab shows Kore.ai Service Role ARN. |
| KMS Key Policy | Verify key policy includes both the root account and BYOK_Role statements. |
| Key Users | Confirm BYOK_Role appears under Key users in the KMS console. |
Contact Kore.ai support and provide the following:
- CMK ARN:
arn:aws:kms:<region>:<your-account-id>:key/<key-id> - Role ARN:
arn:aws:iam::<your-account-id>:role/BYOK_Role
The Kore.ai support team will configure the integration (trust relationship between Kore and your AWS tenant) on their end and notify you when it’s complete.
You can now configure and enable data encryption in Bot Admin Console using your AWS KMS, as explained in the next section.
Configure BYOK Encryption in Platform
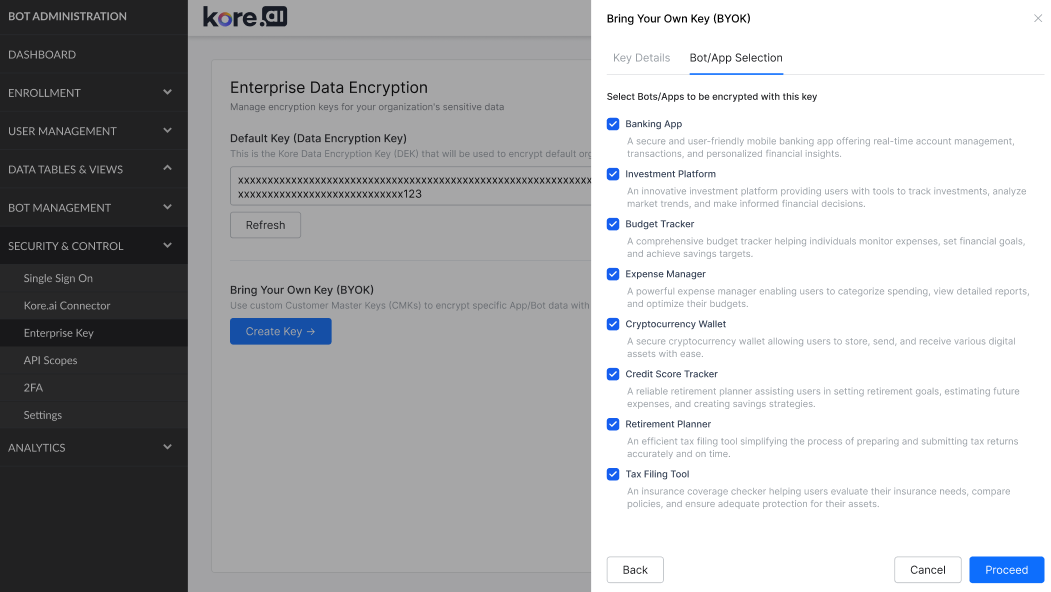
You can enable BYOK encryption by configuring it within the Bot Admin Console. This process connects your AWS KMS key to the Bot Admin Console. During configuration, you can choose which applications and bots will use it.
Configuration Steps
- In the Admin Console, go to Enterprise Key.
- Click Create Key under the Bring Your Own Key section.
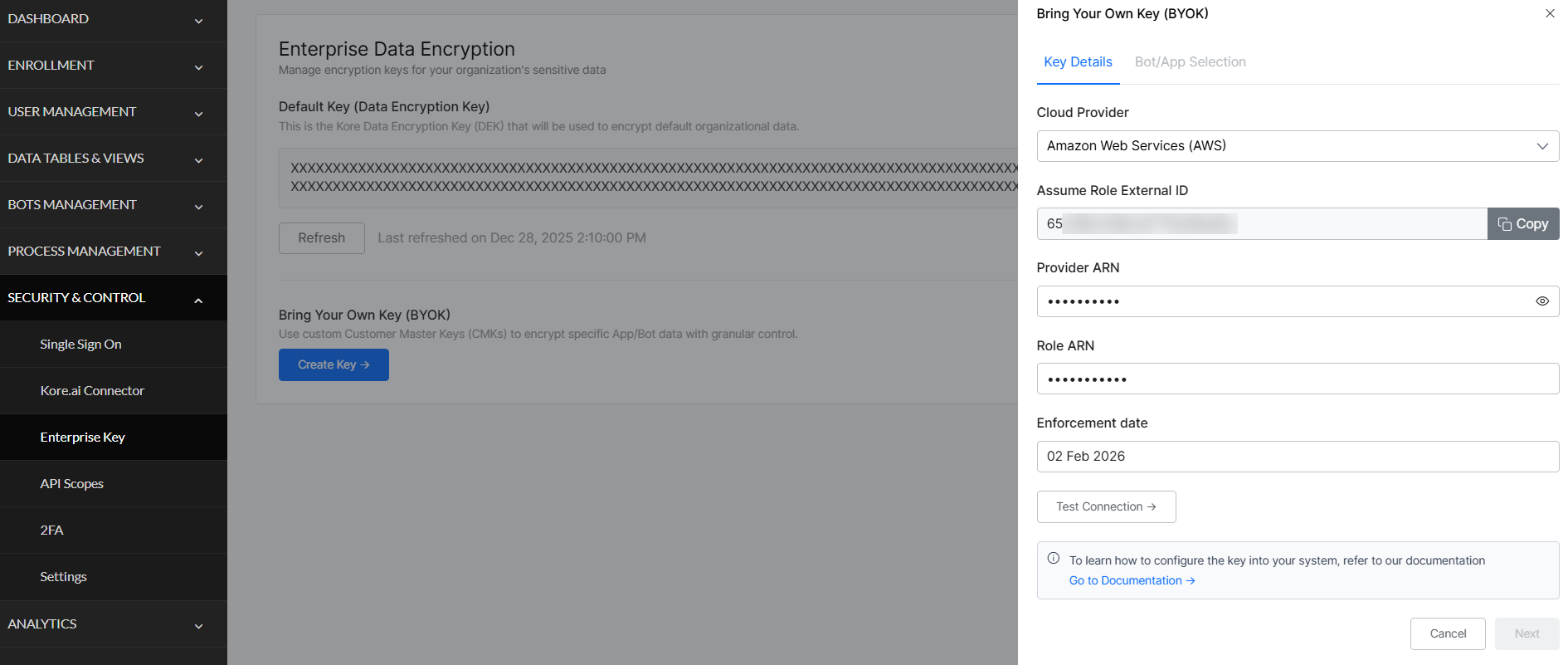
- Enter AWS Details:
- Cloud Provider: Select Amazon Web Services (AWS).
- Assume Role External ID: Auto-populated.
- Provider ARN: Enter your CMK ARN.
- Role ARN: Enter your Role ARN.
- Set Enforcement Date: Choose when encryption will begin. This is the date your CMK starts encrypting data.
Note: You can modify the CMK and retest until the enforcement date. After this date, you can only rotate the key or update which apps/bots are encrypted. - Test Configuration: Click Test Configuration to validate the connection. The system will test the connection to your KMS, authentication, and encryption and decryption operations. Verify all tests pass before continuing.
- Select Apps and Bots: Click Next to view all applications and bots in your workspace.
- Complete Setup: Click Proceed to complete the process. Your CMK is added to the enterprise keys list, and encryption begins on the enforcement date.
Validation (Optional)
After the enforcement date, You can verify that encryption is working by using one of the following options:
Option 1: View Analytics
Check analytics data for recent chat interactions to confirm that encrypted data is accessible.
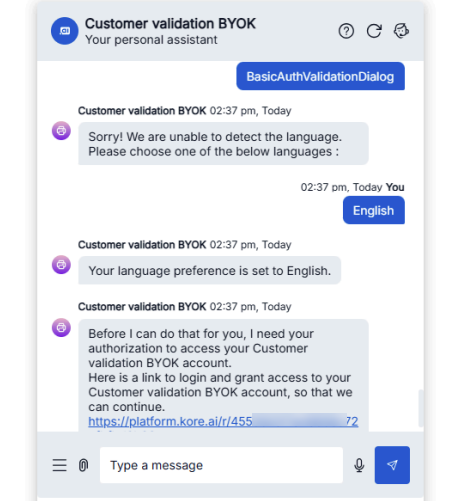
Option 2: Test Application Authorization
Open the application and run Authorization Profiles and Dialogs.
- Execute BasicAuthValidationDialog.
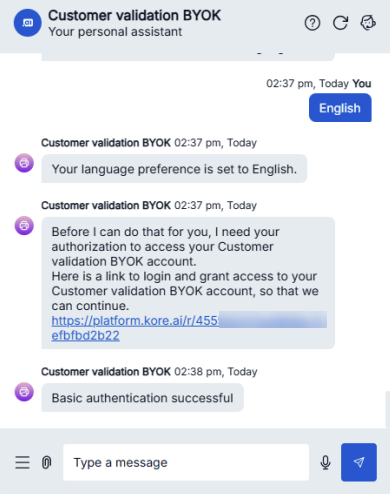
- When the bot displays the authorization link, click the link and enter the credentials (admin/password).
Example:
If successful, the system redirects you and displays “Basic authentication successful.” This confirms your encrypted credentials are correctly stored and retrieved using your CMK.
Related resources